Exciting new features coming to Firebase Auth
Today, Firebase is announcing new security features and functionality to enable you to better secure and manage users, including Multi Factor Authentication, the ability to extend Authentication with requirements specific to your app, and support for new sign in providers. These features are part of an optional upgrade that includes a generous no-cost tier. The upgraded offering will not require a payment method, and the vast majority of Firebase projects will be able to implement these features that bring added security and flexibility to your apps without additional costs.
The new optional upgrade is called Firebase Authentication with Identity Platform. It doesn’t require any migration and you can opt-in with one click in the Firebase console.
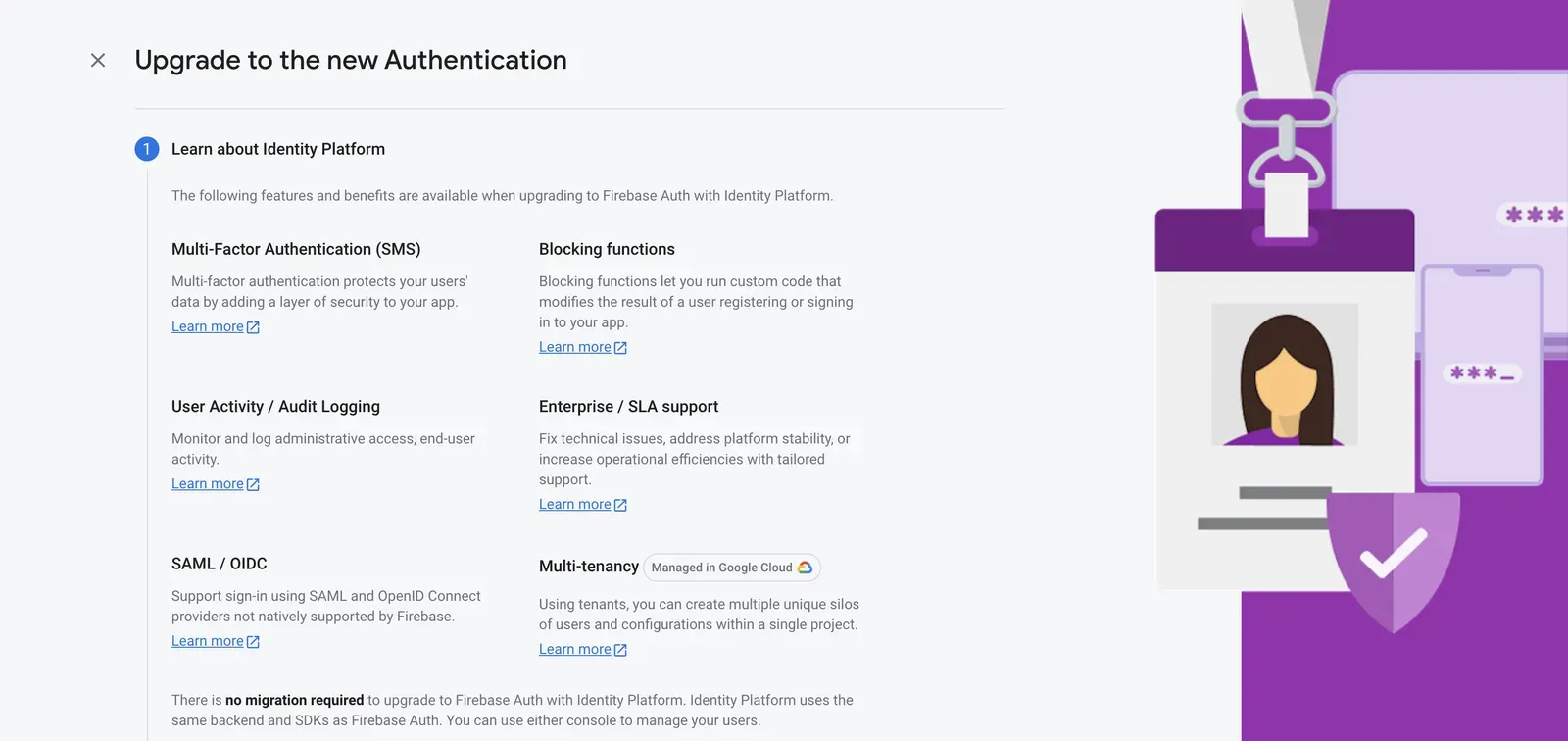
After upgrading, existing Client SDK and Admin SDK code will continue to work as before, and you’ll gain immediate access to features such as improved logging and enterprise level support, which includes a dedicated team with SLAs. With additional code you can add multi-factor auth, functions that let you customize requirements to sign up or sign in, and support for SAML and OpenID Connect providers. Let’s dive into the details!
Extra user protection with Multi-Factor Authentication
Multi-factor authentication has been a highly requested feature. This is where users are requested to provide an additional factor of authentication, in this case, a code sent via SMS, after they sign in. Having a second factor makes it more difficult for attackers to compromise an account, even if they can compromise a password or social account. It’s a great feature that we encourage all developers to implement to protect their users and user data.
Adding MFA to your existing Firebase apps is straightforward. If you’re using FirebaseUI for iOS, Android, Web, or Flutter, MFA support is rolling out to each of those libraries in their next releases. If you’re using the Firebase Auth SDKs directly, learn how to add MFA to your Apple, Android, and web apps.
Extend user management with Blocking Functions
Sometimes you have specific requirements for users to sign up or sign in. For instance, to make an app just for your teammates, you may want to limit users to people with a specific email domain.
Authentication now has support for functions that execute when a user is signing up or signing in. We called them Blocking Functions because they only allow sign in or sign up to be completed once the code in the function finishes executing. Blocking Functions unlock use cases that were previously only available for teams that had the time and resources to implement their own auth servers that would exchange tokens with Firebase Auth. Now all Firebase Auth users can create unique constraints on who uses their app using any logic that you can encapsulate in a Cloud Function.
Some example usages for Blocking Functions are:
- A state or local government could create a function that checks to see if someone lives in that state
- A company could encourage people to disconnect from work by limiting their chat app to people the office by restricting users to specific IP ranges.
- A blocking function could look up a user’s reputation score and then add a new custom claim to the token they issue back to the device for the users with the highest reputation.
With Blocking Functions you can extend Firebase Authentication with any service that can be called via an API. Learn how to in the docs.
const functions = require('firebase-functions');
exports.beforeCreate = functions.auth.user()
.beforeCreate((user, context) => {
// Only users of a specific domain can sign up.
if (user.email.indexOf('@acme.com') === -1) {
throw new functions.auth.HttpsError(
'invalid-argument',
`Unauthorized email "${user.email}"`
);
}
});Sign in users with SAML and OpenID Connect
Firebase Authentication now supports sign-in using Security Assertion Markup Language (SAML) and OpenID Connect (OIDC) providers that are not natively supported by Firebase. We wanted to make sure it was easy to bring in your users from any platform and you can now do this with these self-service providers.
If you’ve been waiting for additional sign in providers like Slack or Discord, your wait is over. By supporting OIDC, we want to empower developers to use the sign-in methods that are best for their customers, without having to wait for custom integrations.
Learn how to add SAML sign-in to web apps and OpenID Connect sign-in to Apple, Android, and web apps.
Improved user activity and audit logging
With the addition of user activity logging, you can now monitor traffic coming into the Firebase Authentication system. For example, you can monitor for drops or surges in Authentication that could signal something going wrong. Because the logs are integrated with Cloud Logging, it’s easy to set up alerts based on thresholds specific to your app, and the logs live with other Firebase logs, for easier debugging.
The new Audit logging lets you know who made configuration changes to your Firebase Authentication instance. This is especially useful for large or growing teams.
When you upgrade your Firebase project, you automatically enable audit logs of changes to auth settings in Cloud Logging. These are things like enabling a new sign in method or other activities that only admins can take. You can also enable logging user auth activity on the Authentication Settings page of the Firebase console; those are events like user sign ins. To learn how to view and analyze your logs, see the Cloud Logging documentation.
Silo your users with Multi-tenancy
Using tenants, you can create multiple unique silos of users and configurations within a single project.
For example, if a customer has built a marketing platform that they sell to other businesses, they may want to use tenants to keep each company’s set of users separate. Each company that uses the marketing platform needs a separate pool of resources and separate sets of identities, but the application that each company uses is the same. With multiple tenants, the customer can house separate sets of identities within one project.
There’s no additional cost for multi-tenancy; it’s included in the upgrade to Firebase Authentication with Identity Platform. Check out the Cloud Identity Platform documentation to learn how to get started with multi-tenancy.
Enterprise support and SLA
We know that running an app is hard. That’s why we have added Enterprise support and an SLA to the new Firebase Authentication with Identity Platform upgraded offering. Enterprise support includes timely responses from a support team that is dedicated to specifically solving customer problems related to Authentication and Identity.
You can rest easy knowing that you will have full support and uptime when using Firebase Authentication for your app.
Usage limits and pricing
Firebase Authentication with Identity Platform is an optional upgrade that adds the above new features to Firebase Authentication. It has different pricing and usage limits compared to the base product:
- Upgraded, no-cost (Spark) plan projects are limited to 3,000 daily active users
- Upgraded pay-as-you-go (Blaze) plan projects are charged for usage beyond the no-cost tier of 50,000 monthly active users.
To better understand your monthly usage, all Firebase projects now have usage charts available for Monthly (MAUs) and Daily active users (DAUs). Before you upgrade, look at your app’s usage. To learn more about the new limits and pricing changes, see the pricing page.
You can upgrade your Firebase Authentication instance today in the Firebase console to get all these features.
